
A security checkup for those utilizing SMB (Scan to Network Folder) solutions with your office’s multi-function printer.
AAA Security — it's not a common term in today’s growing discussions around system and database compromises. But it should be.
These data compromises often occur from email-malware attacks via social engineering. You can Google the term AAA Security for an abundance of information, but essentially it stands for Authentication, Authorization, and Accounting.
Security experts often talk about password changes and password best practices (Authentication). And then there is Accounting (Logging of information about access and resources used by users). However, none of that is as beneficial if you aren’t paying close attention to Authorization.
Here's a Question to Consider.
Who really has access to the files on your computer, even if your screen is locked? Or the files that you scan to your shared network folder during your filing workflows?
During the average installation of a multi-function printer system, a technician will setup 4-5 Scan to Folder solutions when Scan to Email is not being used. One of the steps involved is attended access to the client’s workstation or file server to create and configure a network shared folder that the copier can scan paper documents to in the form of PDF, JPEG, TIFF, etc.
During this process, MANY clients already have a Shared Folder created by them, or their IT department.
Here's Where We See the Vulnerability.
This shared folder (be it server hosted or workstation hosted) will very often be shared with “EVERYONE." This grants access to ANY user on your work group or domain, and likely to any guest that accessed your network; and one who knows the VERY simple steps to discover active hosts on the network.
How about curious internal employees who wonder through the system; whether it be accidental wondering or for other, less innocent intentions?
A common fact for most every organization: Most of the documents that are scanned into a system are of importance, and confidential to the business who is handling the documents. Whether it be tax, financial records, health and wellness, HIPAA-sensitive documents, legal, architectural , proprietary, etc.
It is critical that these organizations grant access only to those who need the access.
Here's One Way to Shore Up Sharing Rights.
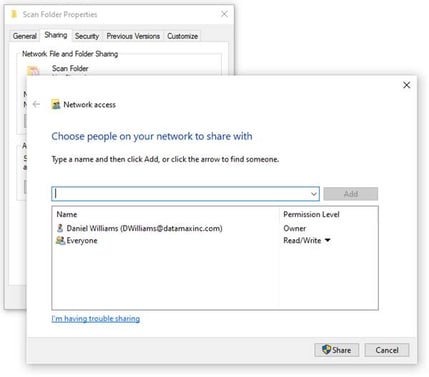 Audit your network shared folder by right clicking and checking its share-tab properties. It will only take a few minutes of your time to ensure that those who need access are listed and those who do not are removed. Protect you and company’s sensitive data from being viewed or deleted by those who should not have access.
Audit your network shared folder by right clicking and checking its share-tab properties. It will only take a few minutes of your time to ensure that those who need access are listed and those who do not are removed. Protect you and company’s sensitive data from being viewed or deleted by those who should not have access.
Any device attached to your network can be hacked. Digital copiers (and many printers) store images of the documents they print and copy on their hard drives. Ready to take a harder look at document security best practices? Consider a Workflow Assessment!


