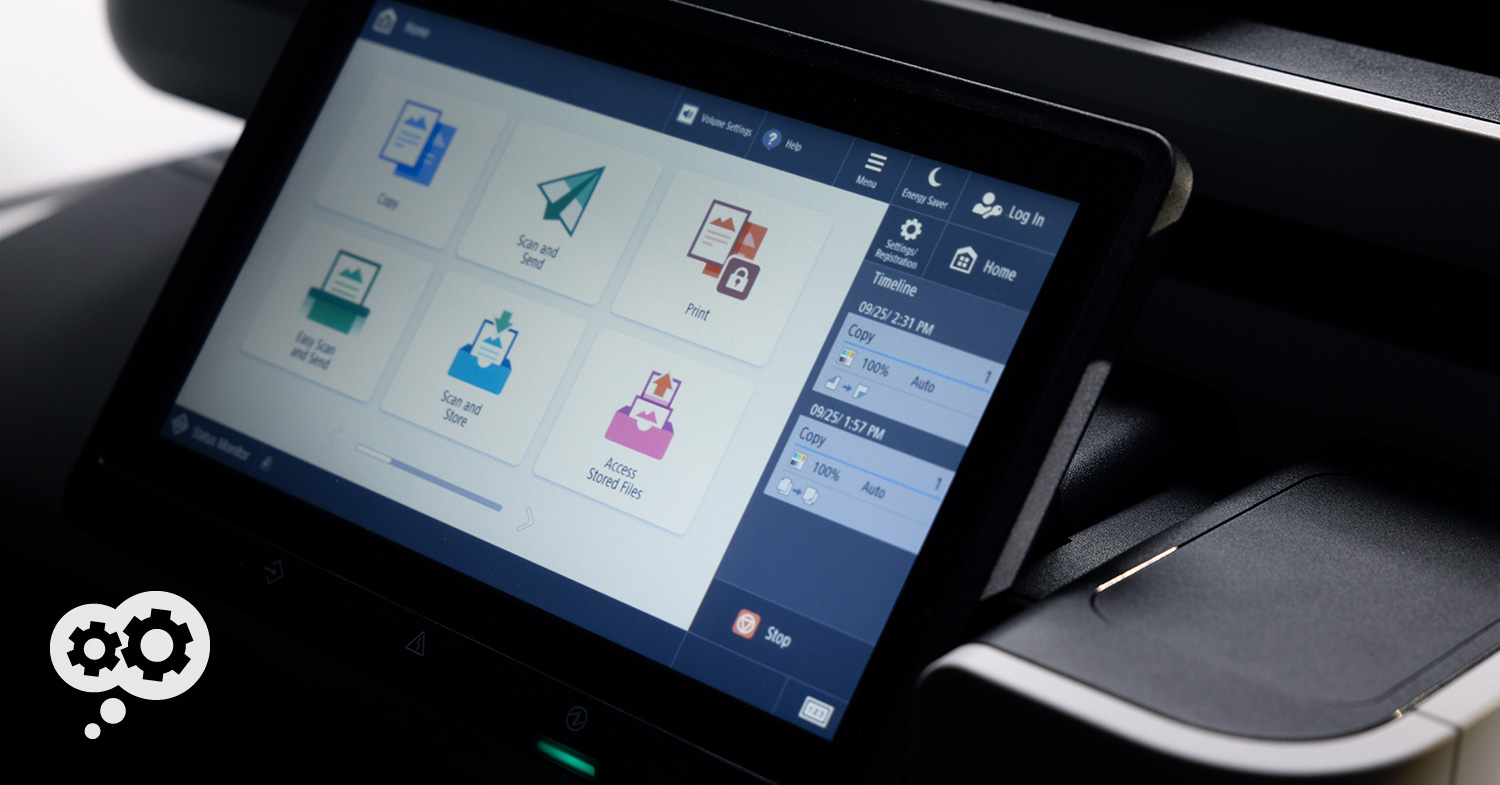
Canon’s new imageFORCE C7165, powered by D² Exposure OLED technology, was built to ensure that trust... and create that impact.
You’ve spent months refining a campaign, choosing the right words, and designing visuals that capture your brand’s energy. Then, the moment your printed piece (maybe it's a limited-time promotion) lands in someone’s hands, the color feels off. The blacks look dull, the logo feels inconsistent, and the impact you worked so hard to create quietly fades.